Introduction
As the digital landscape is rapidly growing. In that situation no one can overstated the importance of network security. The need to connect with interconnected world to grow your businesses has also become an important in this era, when we talk about the connection with interconnected world The Internet, Security may also highly require to make your online connections secure and save from the growing threats of cyberattacks and prying eyes.
Virtual Private Network (VPN) plays its significant role in all that situations where you need to connect your Head office to branch offices or with clients and if your employees working remotely, VPN enhance security and protect your online privacy.
VPN not only protect your personal information but also provide you the freedom of online work in save and secure environment. It enhanced your experience of internet connections by enabling access to increasingly linked world.
What is a Virtual Private Network (VPN)?
A Virtual Private Network or you may call it VPN in short, is a technology that creates a secure and encrypted connection over a less secure network the internet, from your any computed device to a network. It creates a protected tunnel for your data to make it secure from external threats. This technology is essentially required, when your main concern is online security and privacy of your data and you may want to extend your corporate network through encrypted connections.
Why Encryption?
Encryption is the key features of a VPN. All data traffic should must be encrypted when it passes through a VPN between a device and corporate network. It includes all kind of data traffic like confidential emails, business plans, or client information etc. It will remain private and secure as it travels over the Internet. The encryption is a key tool which acts as a barrier against hackers and online dangers.
Types of VPN
You may need to understand the various types of Virtual Private Networks (VPNs) so that you can choose the right one which suits your specific needs. The main types are:
- Remote Access VPN
- Site-to-Site VPN
Remote Access VPN
A Remote Access VPN allows users to connect to a remote network securely over the internet. This type of VPN is used in such a situation where employees and businesses client need to access to their corporate network resources from different geographical locations.
 |
| fig-1: Remote Access VPN |
Key Features of Remote Access VPN:
Secure Remote Connectivity:
Its ability of making the secure and encrypted connection between a user’s device and the remote network ensures that user’s sensitive data transmitted over the internet is protected from unauthorized access and cyber threats.
Flexibility and Accessibility:
Users can access network resources such as files, applications, and internal websites remotely from anywhere, like they were physically present in the office. It enhances the flexibility for remote workers and businesses with a global workforce.
Enhanced Privacy:
By hiding a user's IP address, remote access virtual private networks (VPNs) improve privacy by preventing internet service providers and potential hackers from tracking their online activities.
Use Cases:
Telecommuting:
Ideal for those employees who need work remotely, make their connections secure.
Secure Access for Travelers:
Beneficial for business travelers who need to access their company's resources securely from various geographical locations.
In today's increasingly remote and mobile workforce, Remote Access VPNs are a vital tool since they allow a secure, encrypted access from any location. They guarantee flexible and safe access to company resources for remote working.
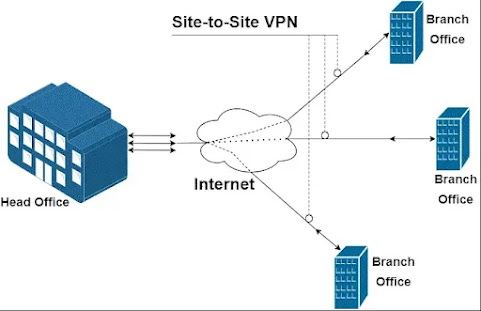
Site-to-Site VPN
A Site-to-Site VPN is a robust solution designed for larger organizations with multiple office locations. Where we need to connect entire networks to each other over the internet. It allows them to establish a unified, secure network across various sites.
 |
| fig-2: Site-to-Site VPN |
Essential Characteristics of Site-to-Site VPN:
Connection from Network to Network:
This will link the network of one office location to the network of another, effectively creating a single, integrated network over long distances.
Enhanced Security for Inter-Office Communications:
Sensitive corporation information remains secure from external threats by encrypting data transmitted between different sites.
Seamless Resource Sharing:
It enables the seamless sharing of resources and services across offices at different geographical locations, improving operational efficiency and collaboration.
Primary Use Cases:
Multi-Location Businesses:
Perfect solution for businesses with branch offices in different geographical locations, required secure, constant communication and resource sharing.
Large Corporations and Enterprises:
Essential for large-scale businesses that need an integrated, secure network environment for all of their units and departments.
